This is a small note to keep the links to posts by Peter Wu:
- Extract pre-master keys from an OpenSSL application
- Extracting openssl pre-master secret from apache2
Example in Debian Buster:
markku@demo:~$ ldd /usr/sbin/zabbix_server | grep ssl
libssl.so.1.1 => /lib/x86_64-linux-gnu/libssl.so.1.1 (0x00007f5f10919000)
markku@demo:~$ dpkg -l libssl* | grep ^ii
ii libssl1.1:amd64 1.1.1d-0+deb10u2 amd64 Secure Sockets Layer toolkit - shared libraries
markku@demo:~$ sudo apt install git make gcc libssl-dev
...
Setting up libssl-dev:amd64 (1.1.1d-0+deb10u2) ...
markku@demo:~$ dpkg -l libssl* | grep ^ii
ii libssl-dev:amd64 1.1.1d-0+deb10u2 amd64 Secure Sockets Layer toolkit - development files
ii libssl1.1:amd64 1.1.1d-0+deb10u2 amd64 Secure Sockets Layer toolkit - shared libraries
markku@demo:~$ git clone --depth=1 https://git.lekensteyn.nl/peter/wireshark-notes
Cloning into 'wireshark-notes'...
remote: Counting objects: 119, done.
remote: Compressing objects: 100% (110/110), done.
remote: Total 119 (delta 8), reused 67 (delta 6)
Receiving objects: 100% (119/119), 1.33 MiB | 3.31 MiB/s, done.
Resolving deltas: 100% (8/8), done.
markku@demo:~$ cd wireshark-notes/src
markku@demo:~/wireshark-notes/src$ make
cc sslkeylog.c -shared -o libsslkeylog.so -fPIC -ldl
markku@demo:~/wireshark-notes/src$ sudo install libsslkeylog.so /usr/local/lib
markku@demo:~/wireshark-notes/src$ sudo systemctl edit zabbix-server
...
[Service]
Environment=LD_PRELOAD=/usr/local/lib/libsslkeylog.so
Environment=SSLKEYLOGFILE=/tmp/pre-master.secrets
markku@demo:~/wireshark-notes/src$ sudo systemctl restart zabbix-server
markku@demo:~/wireshark-notes/src$ ls -l /tmp/pre-master.secrets
-rw-r--r-- 1 zabbix zabbix 7045 Feb 24 20:07 /tmp/pre-master.secrets
With the keys saved by that process (and doing the packet capture at the same time, in either server or client side), you can copy and add the secrets file in TLS preferences in Wireshark:
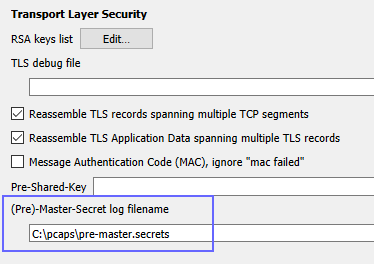
Then you can open the capture file, and see the unencrypted data:
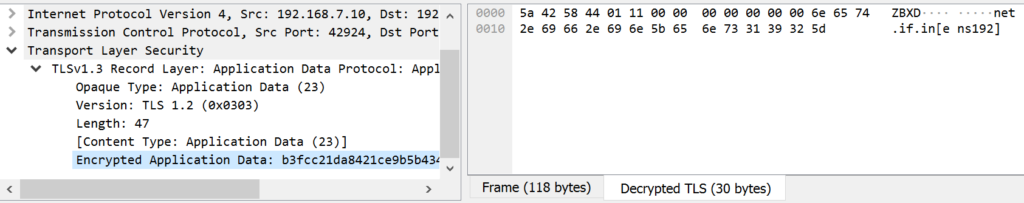
For easier access to the capture file with decrypted data, you can also embed the keys in the capture file by following the instructions in Wireshark Wiki.
Be careful out there when capturing the secrets.